The TYCHON Trace module is now compatible with ePO 5.9 and 5.10 as part of the Automated Continuous Endpoint Monitoring (ACEM) plugin. TYCHON Trace is an advanced feature our customers use to investigate past and real-time activity for forensics, security operations, compliance and troubleshooting endpoints. It provides the ability to visualize and gather information about process creations, network connections, and changes to file creation times.
The Trace module enhances operator decision support systems with valuable data, to include:
- Properties: Data associated with a single executable
- Timeline: Event data in sequence by time
- Loaded Libraries: DLL(s) per executable
- Connection Information: Network source, Destination IP, Source Port, Protocol and Destination Port Data
- Registry Items: Created and modified keys
- WMI Queries: Queries associated to the selected IP address
- DNS Queries: Domain name queries to the selected IP address
- Pipes: Named pipe information
- Files Created: List of files created by the target, including creation time and file name
- Remote Threads: List of threads that are created from an originating process
- External Reports: Advanced Threat Defense (ATD) results
- Tree View: Visual representation of all parent / child processes from the Process Tree and associated event data for each process
The TYCHON Trace module not only provides advanced data, but the data association visuals and advanced data grid displays are easy to use. A quick example of the Tree View can be seen below:
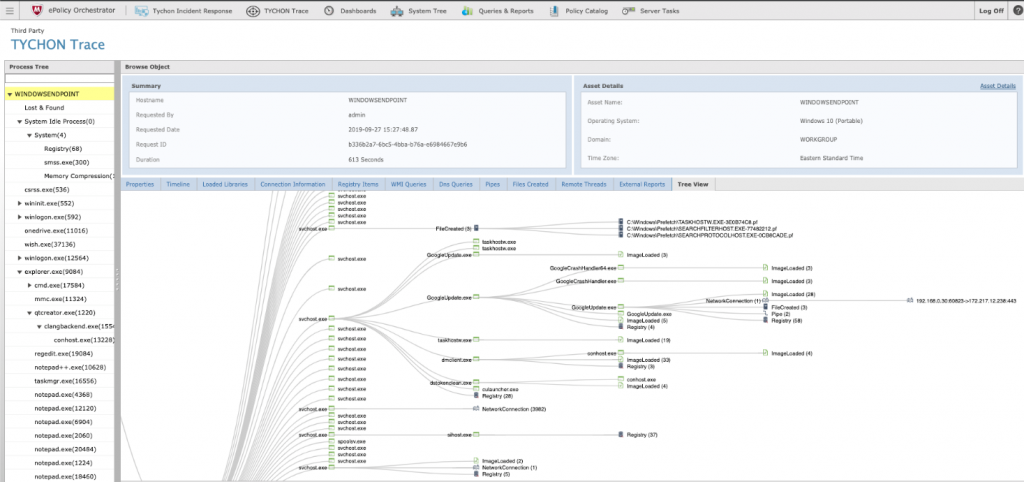
Here you can see how through ePO, TYCHON Trace can visualize any historical endpoint Trace record.
TYCHON Trace is a robust yet simple tool that provides our customers with a powerful set of capabilities. Just a few of the customer use cases that we now bring to McAfee ePO include:
- Hunting for suspicious or malicious activities
- Identifying unauthorized running process activities
- Detecting polymorphic malware communicating to unauthorized DNS / IPs
- Locating registry key changes that indicate compromise
- Saving evidence for future analysis and confirmation
- Visual linkage for network traffic inbound / outbound country location
For more information about TYCHON Trace, please visit our website at tychon.io or contact us directly at info@tychon.io.


