Decrease
your attack surface.
TYCHON Enterprise is an advanced endpoint analytics and remediation platform that aligns to Zero Trust principles. The software delivers real-time endpoint visibility and the capability to proactively monitor, manage, and validate Comply to Connect (C2C) compliance. TYCHON’s dynamic dashboards and streamlined features, enable users to validate security settings, verify users and devices, query endpoint(s), remediate vulnerabilities, add/remove software, quarantine systems, update patches, and more all from a single console. Use proactive validation to strengthen your network access control and decreases your attack surface.
Real-Time Visibility
TYCHON provides interactive dashboards, which display real-time enterprise compliance metrics for up-to-date situational awareness of network risk. These are vital reports with details on privileged users, Web PKI and DMZ, asset inventory, system authorization, HBSS/ESS Services, patching and overall organization software compliance.
Device Hardening
Monitor for exposures, violations, and escalated privileges. Record, index, and actively monitor in real-time. Report, quarantine, and remove outdated operating systems. Identify patch vulnerabilities and remediate immediately. Control standards for installed software and OSs. Achieve all this and more all from a single console.
Enforcement
Remove and disable unauthorized accounts using strong authentication. Verify users and devices, quarantine non-compliant systems, remove unauthorized software, and more.
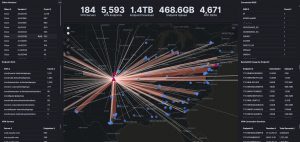
Zero Trust
Use TYCHON’s proactive reporting and automated security features to enhance your situational awareness and enforce Zero Trust principles.
Why TYCHON?
We have experts at the ready
Contact Us to Learn More
"*" indicates required fields

