When it comes to addressing security and compliance across the enterprise, a real time solution is critical to building a network operation that is resilient, proactive, and effective. The speed at which assets on the network change, coupled with emerging and persist threats, warrants a flexible and adaptive approach. To keep pace with an evolving cyber landscape, we need monitoring capability that can produce results in real time, is easy for operators to use, and gets to the information that matters quickly. A capability that can turn questions into answers, and answers into action.
TYCHON’s solution is the Cyber Scorecard (CSC)® Dashboard, a capability for consolidating critical security data from across the enterprise in one fast, easy to use place. The CSC utilizes questions, asked from a command and control application, which are federated across the enterprise to all nodes. Then, TYCHON derives key answers and returns critical information to the interactive CSC Dashboard.
The CSC is built around the security metrics defined in the Department of Defense’s (DoD) Cyber Security Discipline Implementation Plan, designed to measure the effectiveness of cyber security in specific focus areas. These areas include ensuring strong authentication, hardening devices, reducing attack surfaces, and detecting and responding to potential incidents.
The TYCHON CSC directly aligns to the DoD directives by providing the following six key components:
- Web Server Public Key Infrastructure (PKI) and Demilitarized Zone (DMZ) Compliance
- User Logon Evaluation (for all users across the network)
- Host Based Security System (HBSS) Services (including US Cyber Command required point products installed with minimal version active)
- Secure Technical Implementation Guide Checks (based on available Security Content Automation Protocol, content)
- Patches / Updates for All Assets (what patches and updates have been applied from what is available)
- Secure Host Baseline (SHB) (including metrics on whether current host image was created from SHB image, if A/V .dat files have been updated within x amount of days and % of XP/2003 systems online)
The TYCHON CSC is both fast and easy to use. Users run a McAfee Server Task and then navigate to the CSC from the main menu. The CSC provides a single stop for all data returned from the network. Here users can navigate between multiple dashboard panels that align directly to the focus areas mentioned above. Each dashboard provides a unique analysis in the form of chart objects and row level data grid. Additionally, the information is tied together and can be filtered by selecting any chart slice.
A quick example can be seen below, which represents the Web Server PKI dashboard.
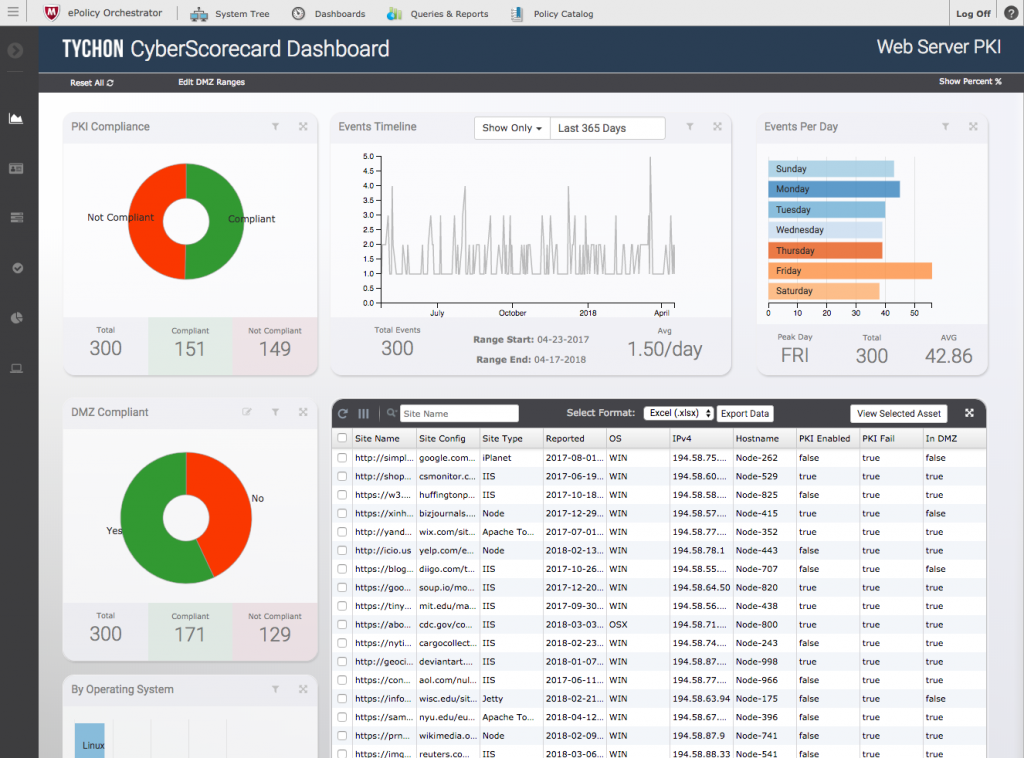
Here we see data from all hosts across the network which have web servers present. You can easily determine which Web Servers are PKI compliant, as well as DMZ compliant. The dashboard also details events over time, provides a comparison by host operating system, and more.
Advanced features let you customize the data to best suit your needs. The timeline filter near the top of the screen allows you to easily adjust the date range of the data. The charts and graphs are interactive, meaning you can click on any chart object slice, for example PKI Not Compliant, and the chart objects and data grid for entire page will update with the newly selected filter. This provides you with a fast, visual way of discerning and filtering information.
The TYCHON CSC is a powerful, yet simple tool that provides operators with critical information fast. When coupled with the EDR capability of TYCHON, this provides a question to answer to action workflow. Users can ask more questions, ask specific questions based on results, take action on those results, and even define their own questions via custom content to fully leverage the capability of the platform! This provides a robust, powerful framework for proactive hunting of threats and remediating them all from the same centralized management interface.


