Why Sniffing Falls Short in Revealing Cryptographic Secrets
In the ever-evolving world of cybersecurity and network analysis, packet sniffers have long been go-to tools for peering into the digital veins of our networks. They capture the raw ebb and flow of data packets, offering insights into traffic patterns, protocol behaviors, and potential anomalies. But when it comes to uncovering cryptographic information—such as encryption keys, certificates, algorithms in use, or even encrypted payloads—packet sniffing hits a wall. This blog dives deep into these limitations, drawing on the OSI model, the anatomy of IP and TCP packets, and real-world comparisons with on-system software agents. We’ll also touch on application libraries to illustrate why sniffing alone often leaves you in the dark, while host-based approaches shine brighter.
Whether you’re a network engineer troubleshooting TLS handshakes or a security analyst hunting for vulnerabilities, understanding these constraints can save you time and guide you toward more effective strategies. Let’s unpack this step by step.
Packet Sniffing Through the Lens of the OSI Model
To grasp why packet sniffers struggle with cryptographic details, we need to revisit the OSI (Open Systems Interconnection) model—a seven-layer framework that standardizes how data moves across networks.
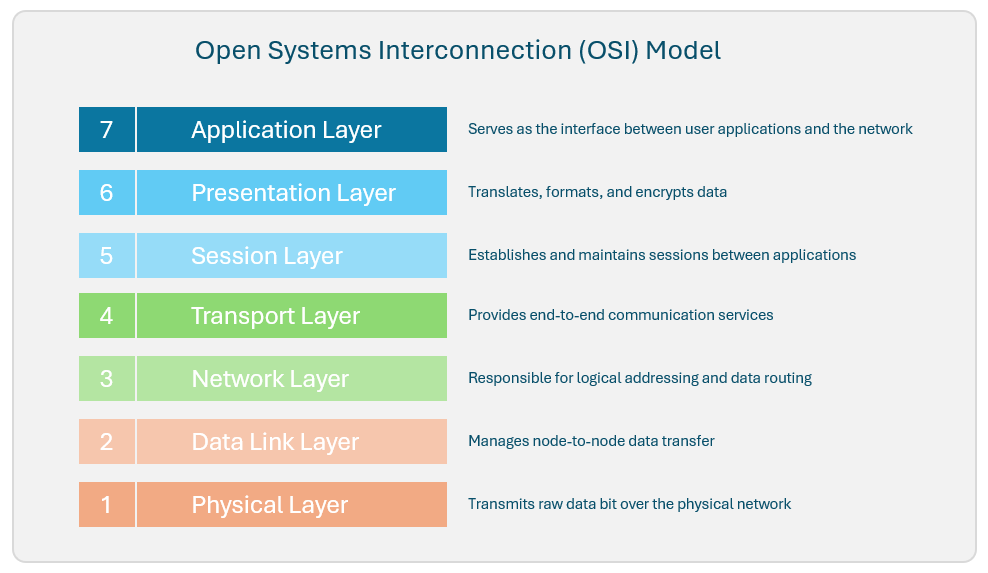
Packet sniffers typically operate at Layers 2 (Data Link), 3 (Network), and 4 (Transport), capturing frames, packets, and segments as they traverse the wire.
- Layer 2 (Data Link): Here, sniffers see Ethernet frames, including MAC addresses and basic error-checking. Useful for spotting ARP spoofing, but crypto encryption happens higher up.
- Layer 3 (Network): This is where IP packets come in, revealing routing info like source and destination IPs. Sniffers can identify if traffic is heading to a known crypto-heavy service (e.g., a VPN endpoint), but they can’t decrypt or analyze the secured content.
- Layer 4 (Transport): TCP or UDP segments show ports, sequence numbers, and connection states. You might infer a TLS session from port 443, but the actual handshake details (like cipher suites) are often obscured if you’re not decrypting in real-time.
The real cryptographic action unfolds at Layers 5-7 (Session, Presentation, Application), where protocols like TLS/SSL encrypt data. Sniffers can capture the initial handshake—exposing server certificates, supported ciphers, and even some extensions like Server Name Indication (SNI)—but once the session key is negotiated, the payload turns into gibberish. Without the private keys or session secrets, you’re blind to the encrypted application data. This is a fundamental limitation: packet sniffing is passive observation from the outside, not an insider’s view into the encryption process.
Dissecting IP and TCP Packets: What’s Visible and What’s Hidden
Let’s get granular with the building blocks of network traffic: IP and TCP packets. An IP packet consists of a header (typically 20-60 bytes) followed by the payload.
- IP Header Components: Source and destination IP addresses, protocol (e.g., TCP=6), TTL (Time to Live), and fragmentation flags. These reveal the “who” and “where” of communication but nothing about crypto. For instance, you can spot traffic to a certificate authority (CA) like Let’s Encrypt, hinting at certificate issuance, but you won’t see the cert’s private key.
- TCP Header Components: Source and destination ports, sequence and acknowledgment numbers, flags (SYN, ACK, FIN), window size, and checksum. In a TLS handshake, the initial SYN packet might indicate a secure connection, and you could analyze timing to detect vulnerabilities like Heartbleed. But the payload—where encrypted data resides—is protected by algorithms like AES-GCM.
Cryptographic information is either in the encrypted payload or not transmitted at all. Private keys, for example, are generated and stored on endpoints, never traversing the network in plaintext. Even public keys in certificates are visible only during handshakes, and modern protocols like TLS 1.3 encrypt the handshake itself after the initial ClientHello. Sniffers might log metadata (e.g., packet sizes indicating key exchanges), but deriving actual crypto params requires side-channel attacks—like timing or length analysis—which are unreliable and often impractical without additional context.
In short, while IP/TCP headers provide a skeleton of the communication, they leave analysts with inferences rather than concrete discoveries.
The Overlooked Challenge: Strategic Placement of Sniffers in Complex Networks
One critical aspect of packet sniffing that’s often underestimated is the sheer complexity of placing sniffers effectively—especially in modern, segmented networks. This isn’t just a technical hurdle; it’s a logistical and financial one that can severely undermine your ability to capture meaningful cryptographic data.
In simple, flat networks, you might slap a sniffer on a switch port and call it a day. But in enterprise or cloud environments, networks are riddled with Network Address Translation (NAT) and even double NAT setups. NAT rewrites IP addresses and ports as packets cross boundaries, like from a private LAN to the public internet. Double NAT adds another layer, common in scenarios like carrier-grade NAT (CGNAT) or nested virtual networks in AWS or Azure.
Here’s why placement complicates crypto discovery:
- Obscured Endpoints: When you sniff post-NAT, the source or destination IPs in the IP header reflect the NAT device’s interface, not the true endpoints. For cryptographic elements like TLS certificates, this means you might see a proxy’s cert instead of the backend server’s—hiding details about the actual encryption endpoint. In a double-NAT chain (e.g., internal NAT to a firewall, then to an ISP NAT), tracing back to the origin becomes a puzzle, as each hop masks the previous one’s identity.
- Segmented Visibility: Crypto data, such as key exchanges, might only be visible in specific segments. For instance, in a VPN tunnel, the outer IP/TCP headers show the tunnel endpoints (often NAT’d), while the inner encrypted payload hides the real crypto handshake. To see the full picture, you’d need sniffers before, at, and after each NAT point—requiring access to routers, firewalls, and edge devices across potentially distributed infrastructures.
- Practical Hurdles: Placement demands physical or virtual taps (e.g., SPAN ports on switches or VPC mirroring in clouds), which isn’t trivial. In regulated environments, this involves compliance approvals, and in multi-tenant clouds, you might not have the privileges. Misplacement could miss crypto flows entirely, like if traffic is load-balanced across unseen paths.
Beyond the technical complexity, it’s expensive: High-throughput sniffers cost thousands, plus ongoing maintenance, storage for captures, and skilled personnel for configuration. Even open source tools can be budget-busting when coupled with the skilled personnel and dedicated hardware required for reliable captures. In contrast, software agents sidestep these issues by residing directly on endpoints, capturing crypto ops without worrying about network topology.
This placement challenge amplifies sniffing’s limitations, turning what should be a straightforward tool into a resource-intensive endeavor. If your network resembles a labyrinth more than a straight line, factor this in early—or pivot to host-based methods.
Strengths and Shortcomings: Packet Sniffing vs. Software Agents
Packet sniffing isn’t all limitations— it has niche strengths over software agents (tools like endpoint detection agents or host-based intrusion detection systems that run directly on the machine). But the contrasts highlight why sniffing alone is insufficient for crypto hunting.

Packet Sniffing
- Non-Intrusive and Network-Wide Visibility: Sniffers don’t require installation on endpoints, making them ideal for monitoring entire networks without alerting users or consuming host resources. You can capture crypto-related traffic patterns, like unusual spikes in encrypted flows that might signal data exfiltration.
- Real-Time, Passive Capture: They excel at live analysis, spotting anomalies like weak cipher usage in TLS negotiations before data is encrypted.
- Cost-Effective for Broad Surveillance: No need for agent deployment across fleets; one sniffer on a switch can cover multiple devices—though, as noted above, this “cost-effectiveness” evaporates in complex setups.
Software Agents
- Direct Access to Secrets: Agents can inspect key stores or hook into API calls to reveal keys in use—something sniffers can’t touch since keys don’t hit the wire.
- Decryption Capabilities: Tools can decrypt traffic on the fly by accessing session keys from memory, bypassing network encryption.
- Contextual Depth: Agents see the full application stack, including how crypto is implemented, whereas sniffers are limited to observable network artifacts.
Overlaps and Why They Matter
There’s notable overlap: Both can monitor traffic volumes and protocols. For example, a sniffer might flag high-entropy packets (suggesting encryption), while an agent confirms it by tracing back to a process like OpenSSL. This synergy is powerful in hybrid setups—use sniffing for initial triage, then agents for deep dives. However, the overlap underscores sniffing’s weakness: It provides breadcrumbs, but agents follow them to the source. In crypto scenarios, where secrets are host-bound, agents win hands down—especially when sniffer placement adds layers of complexity and cost.
A Case Study in Discovery Limitations
Microsoft’s ecosystem is built on cryptographic libraries like CNG and the legacy CryptoAPI, used by applications ranging from Edge (TLS) and Outlook (S/MIME) to Azure services (key management). Let’s imagine a packet sniffer is this environment.
- Sniffer Limitations: A packet capture shows the protocol surface — e.g., in TLS ≤1.2, you might see certificate chains or ECDSA signatures. In TLS 1.3, however, certificates and signature details are encrypted, so that visibility is lost. Either way, sniffers cannot reveal:
- Whether an app internally used SHA-1
- How keys were generated
- Whether keys are rotated or stored securely
Certificate thumbprints can be extracted offline from cleartext chains, and revocation status may sometimes be inferred (e.g., via OCSP stapling), but full runtime cryptographic behavior remains opaque. In NAT or proxy-heavy networks, even the visible elements may reflect intermediaries rather than the true endpoint.
- Advantages of On-System Software Discovery: Tools that hook directly into CNG calls reveal functions like BCryptGenerateSymmetricKey or NCryptExportKey. This exposes the exact algorithm (e.g., AES-256), key lengths, and even potential weaknesses like hard-coded keys. For apps, agents can audit the Windows Certificate Store or registry entries for crypto configs—far beyond what network metadata offers. In forensics, this means reconstructing encrypted sessions from memory dumps, something impossible with pure sniffing.
The takeaway? For tech-savvy teams dealing with complex environments, on-system discovery isn’t just advantageous—it’s essential. It turns opaque network blobs into actionable intelligence, reducing blind spots in audits or incident response.
Wrapping Up: Beyond the Wire for True Crypto Insights
Packet sniffing remains a cornerstone of network forensics, but its limitations in discovering cryptographic information are profound: Encrypted payloads stay hidden, host-bound secrets are inaccessible, inferences from IP/TCP headers are often too vague, and now we’ve seen how sniffer placement in networks adds insurmountable hurdles in terms of effort and expense. While it edges out software agents in non-intrusiveness and broad visibility, the overlaps favor hybrid approaches, and on-system methods dominate for depth.
If you’re building a robust security toolkit, don’t rely on sniffers alone. Integrate host agents for that insider edge and plan your network taps meticulously to avoid costly pitfalls. After all, in the crypto game, seeing the packets is one thing; unlocking their secrets is another.
What are your experiences bridging these gaps? Share in the comments.


