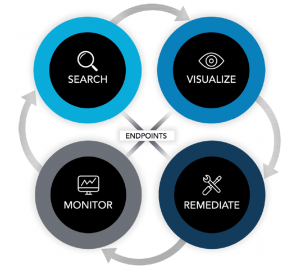
Take control of your endpoints.
Poor visibility is a problem of the past. Use TYCHON to search, visualize, remediate, and monitor security concerns across all your endpoints within one powerful interface. Decrease your enterprise attack surface and strengthen your operational resilience.
Search
Get your data from the source.
- Retrieve intelligence from your endpoints with precision and speed
- Leverage an embedded search engine for optimized query response
- Use natural-language questions to query endpoints
- See results in seconds, not hours
- Access lifetime data records for every endpoint

Visualize
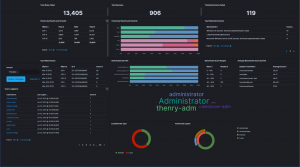
Fine-tune your analysis.
TYCHON includes built-in analytics, reports, and dashboards to help you analyze individual devices or hundreds of thousands at a time. Choose from our pre-built visualizations and tools or design your own to track Asset Inventory, Patch Status, Security Services, Vulnerability Status, and more.
Remediate
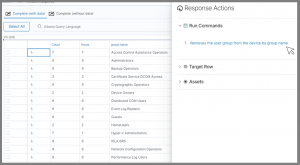
Take action with a single click.
- Quarantine non-compliant systems
- Deploy patches
- Update registries
- Delete files
- Kill processes
- Disable unauthorized accounts
- Add or remove software
- Alter software and OS configurations
Monitor
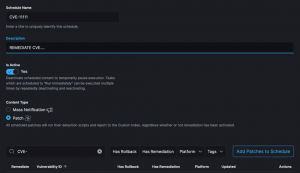
Upgrade your situational awareness.
Review system activity and gather information about network changes. Verify HIPAA, PCI DSS, NIST, and STIG configurations. Get alerts on new CVEs. Verify patch installs. Enforce Comply to Connect
ENDPOINT MANAGEMENT WILL NEVER BE THE SAME.
Our low overhead sensor and innovative mesh model enables instant queries from up to 1 million endpoints at a time.

TYCHON SENSOR
Monitor thousands of attributes
from every endpoint

TYCHON MESH MODEL
Complete targeted searches
in milliseconds

OPEN ARCHITECTURE
Deploy third-party integrations and
build custom queries
Why TYCHON?
We have experts at the ready
Contact Us to Learn More
"*" indicates required fields

