Recent Symmetric Encryption Changes Highlight the Need for Holistic Cryptographic Monitoring
Network-only monitoring solutions cannot effectively track enterprise-wide cryptographic operations. Comprehensive discovery of cryptographic assets requires visibility into both network traffic and endpoint activities. Network monitoring provides valuable insights into data in transit, but it cannot detect cryptographic operations that occur locally on endpoints. This limitation is particularly evident with symmetric encryption algorithms like Advanced Encryption Standards (AES), which are frequently used for file encryption and secure data storage before transmission.
Consider a common scenario where an employee encrypts sensitive files using AES encryption before sharing them through standard communication channels. Without endpoint visibility, organizations would only see the encrypted data traversing the network, missing crucial information about the encryption process and AES implementation. This creates a significant blind spot in cryptographic visibility and security assessment, as highlighted by the dotted lines in the following workflow example.
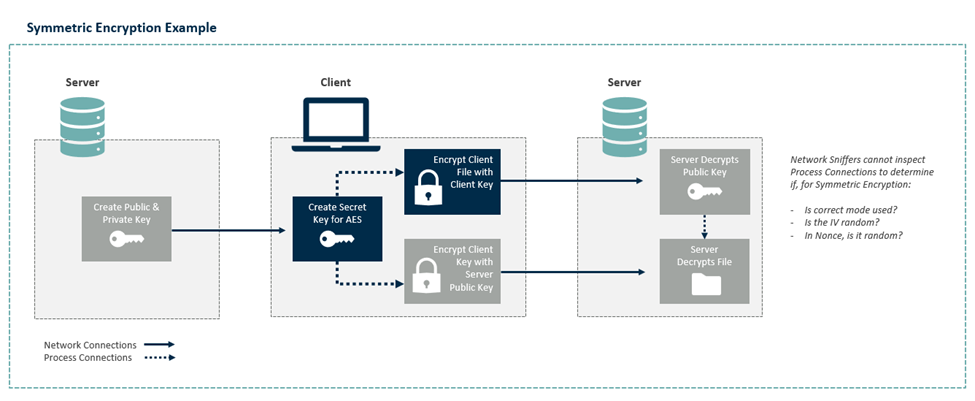
The pending updates to AES standards emphasize the critical importance of maintaining robust security through proper implementation and monitoring. To achieve compliance with these standards and ensure cryptographic security, organizations must first establish complete visibility into where and how AES is being used across their infrastructure.
TYCHON’s Automated Cryptographic Discovery and Inventory (ACDI) technology serves as an essential tool in this mission, providing detailed insights into cryptographic operations at their source, without installing any new processes. TYCHON ACDI detects and monitor various implementations of AES or any symmetric algorithm, including custom applications, third-party software, and built-in operating system features that utilize encryption and provides critical visibility and situational awareness to the organization of the cryptography that secures the enterprise and defends the mission.
With the distribution of modern enterprises, including remote workers and cloud services, endpoint visibility is more crucial than ever. Network-only monitoring solutions cannot effectively track cryptographic operations that occur outside the corporate network perimeter. TYCHON’s lightweight endpoint scripts bridge this gap by delivering not just network-based information, but also continuous visibility regardless of location, ensuring that organizations maintain oversight of their cryptographic assets and operations. TYCHON’s holistic approach enhances security and supports compliance efforts by providing detailed documentation of cryptographic implementations across the enterprise.


